General Reminders and News
Peak M-Pathways System Usage Beginning of Fall Term
The beginning of a new academic year is always a time of heavy system usage. The peak period during which students drop and add classes is anticipated to begin on Monday, August 30 and continue through the drop/add deadline on Monday, September 20.
Enroll/Update UM Emergency Alerts
UM Emergency Alerts are mass notifications used solely in the case of a campus wide alert that keep students, faculty and staff informed about major active emergencies. Examples of situations where a notification may be sent are a tornado warning, potential life threatening incident, hazardous spill, campus emergency, weather-related or other class cancellations. For additional details, see the UM Emergency Alert page.
Human Resource Management System
Enter Telework Status
The Enter Telework Status instructions, available in My LINC, have been updated to reflect a new business process for Maintaining Telework Agreements in M-Pathways Human Resource Management System. Specifically, if an employee indicates working outside of the state of Michigan, then the user needs to verify the employee's country and state. The new public query, M_HR_CURR_ADDRESS_STATE_CNTRY, assists users in the verification process by providing the country and state of the employee's current address.
My LINC adds LinkedIn Learning and Business Objects Reporting
U-M staff and faculty have new learning and reporting opportunities in My LINC with the addition of LinkedIn Learning courses and data reporting in Business Objects. ITS has partnered with Organizational Learning and Information Quest to improve personal and professional development and help make data-driven business decisions.
Business Objects Reporting
My LINC data is available in Business Objects so departments and units can run the reports they want to run, when they want to run them. This data can be used to make better business decisions and inform future strategy.
Several pre-built reports are also available:
- User Training by Department Code
- User Training by Activity
- User Training by Activity and Department Code
- User Training by Uniqname
To access the My LINC data, users need to submit a request via the Online Access Request System (OARS) for the My LINC Data - BO (MLNC) role. Information about the My LINC data is included in the Human Resources Data Dictionary.
LinkedIn Learning
LinkedIn Learning (formerly Lynda.com) has been integrated into My LINC, allowing the U-M community to access content from industry experts in software, creative, and business skills. Individuals can use LinkedIn Learning to guide their own professional development, or units and departments can focus on a specific topic by directing staff to training.
LinkedIn Learning courses taken through My LINC display on users’ transcripts and are included in the My LINC Business Objects data set.
Student Administration
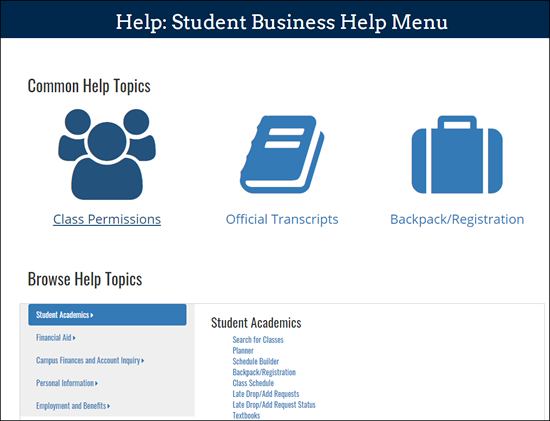
Assisting Students? View Student Business Help Pages
The Student Business, Student Center is a primary resource for academic, financial, and personal transactions. When assisting students, you can view the associated Student Business Help pages. In My LINC, search on keyword 'Student Business Help' for a link to the menu.
The help pages contain documentation and simulations for many student transactions. In Student Business, the Help link on the Student Center page opens this same menu. Specific transaction help is linked from other Student Business pages.
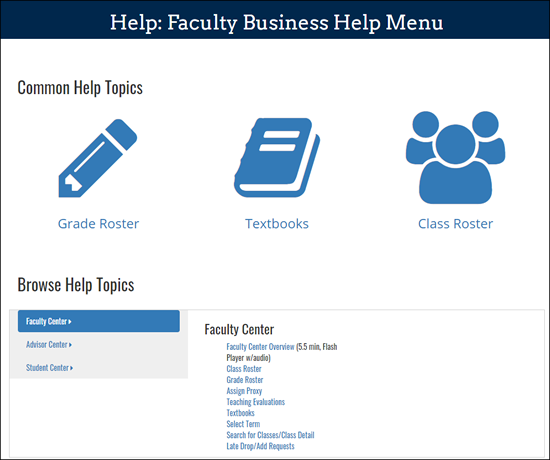
Assisting Faculty? View Faculty Business Help Pages
The Faculty Business Help pages contain documentation and simulations for many teaching and advising related transactions. In My LINC, search on keyword 'Faculty Business Help' for a link to the menu.
In Faculty Business, the Help link on the Faculty Center page opens this same menu. Specific transaction help is linked from other Faculty Business pages.
Safe Computing
How to Spot Misleading Sender Addresses
Email with forged or misleading sender addresses, sometimes called "spoofs," can be one of the harder types of email scams to catch.
Email spoofing is when the scammer tries to make the email appear to come from a known and trusted source. The goal is to convince you to do things like reply with personal information, visit a malicious website, or send money. The good news is, with a little effort, you can spot most spoofs.
Here are a few good ways to spot a spoof:
-
Compare the email address with the display name. Often the name will be familiar, but the actual address will not be.
-
Check the name and address against a previous email from the same sender.
-
Check the spelling. Scammers often change a single letter in the name of the person they are impersonating or insert a special character to make the name look correct at a glance.
-
Compare the From and Reply-To addresses. Be suspicious if the From address is clearly a U-M address, but the Reply-To address is not!
-
Check that email from someone at U-M is from a umich.edu address. Lots of spoofs impersonate notable U-M faculty and staff to try and scam folks in the university community!
Visit How to Spot a Spoof on Safe Computing for other clues to help you catch spoofs. You can see Phishes & Scams that have been reported at U-M for examples and descriptions of email scams reported by folks around the university. And check out the main Phishing & Suspicious Email page for lots of tips on catching phish before they catch you!
Protect Yourself and the U Against Ransomware
Ransomware is on the rise and you have an important role to play in protecting U-M! Cybercriminals continue to target universities, healthcare providers, and other organizations. See the In the Media section of Safe Computing to learn about the many ransomware attacks that have occurred over the past year.
Ransomware attempts often begin with a phishing email. When the recipient opens an attachment or shared document or visits a malicious website, ransomware or other malware is installed on their device. It can then infect and encrypt files on their device or systems they connect to. In other cases, attackers gain access to install ransomware on a system that is exposed to the internet or through vulnerabilities in software that is not kept up-to-date
Once systems are infected, the threat actor demands a ransom (usually to be paid through cryptocurrency) to restore your access. They may also threaten to publish or delete the data if the ransom is not paid.
You can help protect yourself and the university from ransomware by doing the following:

-
Recognize and avoid falling for phishing and suspicious email.
-
Secure your devices by keeping your software up-to-date. Apply software updates promptly, and ensure that security software (such as antivirus) is running and up-to-date.
- Back up your data. See Back Up U-M Data for requirements if you are responsible for managing university data and/or systems that store it.
See Ransomware: Don't Pay the Ransom! and Ransomware Mitigation for additional details, and print and post this 8-1/2 X 11 inch poster—Poster: Beware of Ransomware!. Digital signs are also available.